Offer description
IAPP’s CIPT training and certification offerings include the following:
. 14-hour live training, online with a trainer
. Quiz to prepare the CIPT certification by the IAPP
. “Voucher” you can use to take the CIPT certification in a Pearson VUE center
. Participant guide
. 1 year membership to the IAPP
FINANCING
Contact us for a quote.
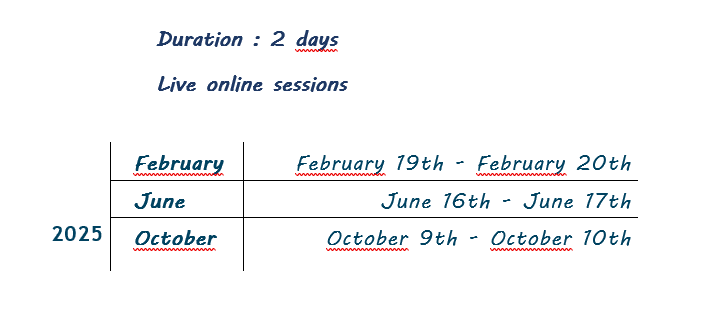
MODALITY
Distance learning takes place through the Webex video conferencing tool
Prerequisites
To have professional experience working in computer science in a business environment.
To understand and to know how to use Office Software Application Tools (MS Office kit, internet browsers, Android and Windows OS).
To have an interest and a good working knowledge of digital technologies.
You need to have a working knowledge of business English.
Objectives
1. To master critical concepts and practices in relation with ICT Data Protection
2. How to Answer consumers’ Data Protection expectations.
3. How to Integrate Privacy Protection in the conception of products and technology services to control costs, accuracy and speed at which they will be available on the market
4. How to Build protection practices regarding data collection and transfer
5. How to Foresee Data Protection problems in IOT.
6. How to take into account Data Protection in data classification and new technologies
7. How to communicate on data protection questions with partners such as the board of directors, development, marketing and judicial teams.
Training content
Module 1: Foundational principles of privacy in technology
Summarizes the foundational elements for embedding privacy in technology through privacy by design and value-sensitive design; reviews the data life cycle and common privacy risk models and frameworks.
Module 2: The role of the technology professional in privacy
Reviews the fundamentals of privacy as they relate to the privacy technologist; describes the privacy technologist’s role in ensuring compliance with privacy requirements and meeting stakeholder privacy expectations; explores the relationship between privacy and security.
Module 3: Privacy threats and violations
Identifies inherent risks throughout the stages of the data life cycle and explores how software security helps mitigate privacy threats; examines the impacts that behavioral advertising, cyberbullying and social engineering have on privacy within the technological environment.
Module 4: Technical measures and privacy-enhancing technologies
Outlines the strategies and techniques for enhancing privacy throughout the data life cycle, including: identity and access management; authentication, encryption, and aggregation; collection and use of personal information.
Module 5: Privacy engineering
Explores the role of privacy engineering within an organization, including the objectives of privacy engineering, privacy design patterns, and software privacy risks.
Module 6: Privacy-by-design methodology
Illustrates the process and methodology of the privacy-by-design model; explores practices to ensure ongoing vigilance when implementing privacy by design.
Module 7 : Technology challenges for privacy
Examines the unique challenges that come from online privacy issues, including automated decision making, tracking and surveillance technologies, anthropomorphism, ubiquitous computing and mobile social computing.
Exam and certification
Once Data Privacy Professionals has given you the “voucher”, the steps to obtain the certification are the responsibility of the IAPP:
1. Registering for the exam directly by phone or on the IAPP website,
2. Book an appointment to take the exam at a Pearson VUE test center,
3. Take the Exam.
At the beginning of the training course, the participant will register for the exam with Pearson VUE. This exam is not mandatory but allows you to obtain the CIPT certification. The CIPT is a MCQ exam of 70 questions and 20 non-graded questions, some are based on scenarios. The score for CIPT certification is 300 out of 500 points.
Intended audience
· Data Protection Officer (DPO)
· IOT Manager
· Document manager
· System developer
· Security and IT specialist
· Any person building and developing IT systems.